Post-Quantum Cryptography (PQC) is transforming the Hardware Security Module (HSM) landscape as vendors prepare for a future where quantum-safe security becomes mandatory. Although adoption is still early, crypto-agile and next-generation architectures are laying the groundwork for a full transition to PQC within the next decade.
Post-Quantum Cryptography (PQC) is an emerging topic across the Hardware Security Module (HSM) value chain. With Cryptographically Relevant Quantum Computers (CRQCs) around the corner, the cybersecurity industry is increasingly introducing advanced PQC algorithms into solutions.
While the National Institute of Standards and Technology (NIST) standardized four PQC algorithms last year, and others are on the way, there is still much work to be done. HSM vendors, for all their efforts, have yet to reach a critical mass in offering PQC to their end users and in integrating PQC into their hardware architectures. Working against them is the time-consuming certification process and limited demand for quantum-resistant security.
Classical algorithms still reign supreme across industries. This has put crypto-agile hardware security modules in the spotlight, allowing customers to choose when and how they want to leverage legacy cryptographic algorithms or PQC algorithms, or even hybrid schemes.
Eventually (sometime around 2035 to 2040), organizations will have no choice but to migrate to PQC-capable solutions. Leading HSM vendors like Crypto4A, Entrust, Marvell, Utimaco, and Thales are already preparing for that post-quantum future.
Key Takeaways:
- PQC is the future of HSMs. Adoption of PQC-architected hardware security modules will be slow because most HSM certifications don’t require quantum-safe designs and the lion’s share of vendors still use classical algorithms internally.
- Most HSM vendors are only in external PQC support. Almost all HSM vendors offer firmware updates for pre-standardized algorithms, with some having already achieved CAVP certification from NIST for their PQC libraries. Most users are leveraging these in test environments today.
- True quantum-safety requires deep internal changes. HSM vendors must secure firmware, boot processes, authentication mechanisms, and secure communications with quantum-safe methods, likely to be with hybrid schemes that combine classical and PQC algorithms.
- Crypto-agile HSMs will guide the transition. Crypto-agility enables both the vendors and their end customers to keep using classical algorithms while preparing for mandatory PQC in the 2035 to 2040 window.
Internal PQC Support Isn’t Technically Mandated for Hardware Security Modules…Yet
Quantum-safe architectures for HSMs will become the de facto standard, but the path will be slow and uneven. ABI Research expects most quantum-safe HSMs to roll out gradually across the next decade. Widescale support is likely within the 2035 to 2040 time frame.
Our cautious outlook reflects the conservative nature of the HSM market over the past 3 decades. You have to remember that PQC represents a seismic shift for the cryptography industry, and this includes HSM manufacturers, requiring expensive and time-consuming standardization and technological upgrades in both hardware and software. Given that PQC certification programs like Federal Information Processing Standards (FIPS) 140-3 and Common Criteria (CC) Evaluation Assurance Level (EAL) do not yet require quantum-safe architectures, there is limited incentive to redesign internal HSM foundations today, with vendors focused on supporting PQC for external use by clients.
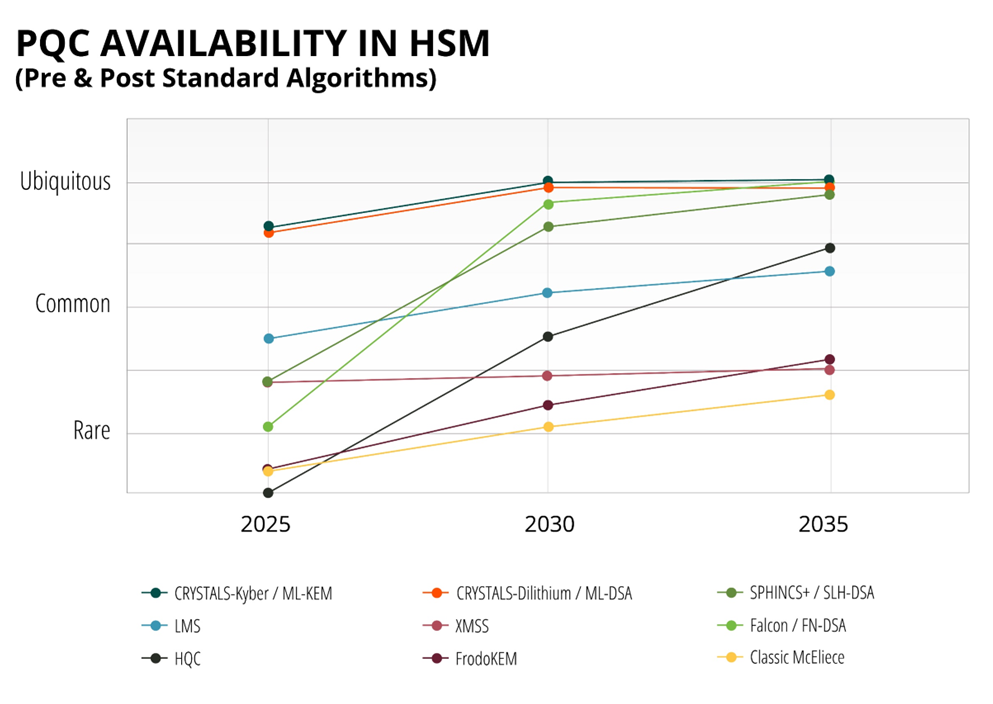
Like any company, hardware security module vendors’ product strategy aligns with customer demand, of which PQC still takes a backseat to classical algorithms. Most HSM vendors are instead adding PQC libraries through firmware updates to support both pre-standard and standardized algorithms. This is facilitated through early access programs, and a few have production releases for current generation HSMs. While many HSM manufacturers are building their own PQC libraries, a smaller group have opted to leverage third-party Intellectual Property (IP) from IP providers that have already gone through CAVP certification for NIST standardized algorithms (ML-KEM, ML-DSA, SLH-DSA, LMS).
Takeaway: PQC is undoubtedly the future of HSMs, but support, either internal or external, is currently not required to continue doing business. Security vendors are more largely preoccupied with obtaining certifications (FIPS 140-3 CMVP and CAVP for FIPS 203, 204, and 205) and catering to clients who use classical algorithms.
Which Hardware Security Module Manufacturers Are Leading the PQC Charge?
Despite the lack of a clear quantum-safe mandate for HSM architectures, the race to build the next generation of FIPS 140-3 certified HSMs is well underway. Four vendors (Entrust, Marvell, Thales, and Utimaco) have achieved it thus far. Although it is a necessary step in the right direction, none of them support PQC architectures. Most HSM manufacturers are working through the drawn-out CMVP validation process to certify next-generation HSMs, that will in time include support for standardized PQC algorithms, but not necessarily quantum-safe architectures.
When I said it’s a drawn-out process, I wasn’t exaggerating. On average, it takes more than 2 years from lab submission to certification under FIPS 140-3. Most vendors are currently in testing or under review, with final approvals expected in 2026 or 2027. In the meantime, many have secured CAVP validation for their PQC libraries and offer early access to end users.
Crypto4A has gone further than any other hardware security module manufacturer by embedding PQC deep into its architecture. The company uses a fully integrated quantum-safe design. Its Quantum Assured Security Module (QASM) architecture supports hybrid Roots of Trust ( RoTs), PQC-secured boot processes, and layered key protections across firmware, authentication, and storage.
IBM, although not strictly an HSM vendor, is also notable for using hybrid schemes for the HSM firmware update process for its z16 HSMs. It uses Dilithium and Kyber algorithms for secure boot and firmware validation. Also in the mix are Futurex and Entrust, which are progressing on similar paths, focusing on cryptographic agility.
While nearly all HSM vendors now offer PQC algorithm support, very few have redesigned the underlying architecture for it. ABI Research expects more firms to cross that threshold between 2026 and 2027 as standardization matures and client demand sharpens.
Takeaway: Hardware security module vendors are increasingly incorporating PQC algorithm support, though most implementations remain at an early or limited stage. Crypto4A is the only vendor to have commercially launched HSMs with a genuinely quantum-safe architecture. Early movers will find quick wins across highly sensitive verticals like government, financial services, and healthcare.
The Difference Between Supporting PQC Internally and Offering PQC-Capable HSMs
Selling more products is, of course, the end goal of hardware security module vendors. Offering PQC-supported security solutions will be essential to meeting future customer demand. But just as important is supporting PQC within internal architectures. This process requires HSM vendors to bake quantum resistance into the entire end-to-end ecosystems they have developed for their HSMs.
- Design and Development: Next-generation HSMs must use PQC algorithms throughout the entire cryptographic chain. Merely exposing cryptographic algorithms through Application Programming Interfaces (APIs) will not be enough to safeguard against CRQCs. For HSM manufacturers, this means applying PQC to root signing keys, internal key wrapping, and key exchanges.
- Firmware Security and Secure Boot: Firmware must be authenticated with quantum-safe signatures and verified against PQC-based trust anchors. HSM vendors should use PQC algorithms or hybrid schemes for secure boot, validation updates, and root key protection. That way, they can verify that the entire firmware chain will withstand future cryptographic advances.
- Hardware Acceleration, Performance, and Storage Optimization: PQC introduces larger key sizes and more computational overhead. Therefore, HSM companies will require dedicated hardware acceleration to maintain acceptable latency and throughput. Vendors must redesign hardware to support more efficient hashing, padding, and seed-based key generation to reduce memory demands.
- Lifecycle Management: Quantum-safe HSMs must manage the generation, storage, backup, and destruction of both classical and PQC keys. Hybrid key infrastructures will be essential for identification, attestation, and secure export during disaster recovery.
Takeaway: As organizations gradually migrate to PQC, HSM vendors cannot simply market their products as “quantum-safe” and call it a day. True PQC claims can only be validated if the vendor embeds quantum-resistance across the entire lifecycle, from manufacturing to software updates.
Crypto-Agility as a Bridge to Quantum-Safe HSMs
If an HSM vendor took all the steps above without supporting crypto-agility, it would be all for naught. As already mentioned, the transition to PQC-supported HSMs will be gradual. Most organizations will continue to use classical algorithms like RSA and ECC for the next decade.
And why wouldn’t they? Why would you pay for all the bells and whistles of PQC if you don’t have to? The Return on Investment (ROI) is elusive.
Outside of a select few verticals, quantum resistance is mostly a nice-to-have. ISACA finds that just 5% of technology and cybersecurity professionals consider quantum computing in their near-term planning.
Until companies are forced to adopt PQC, classical algorithms will remain popular. However, at some point, classical algorithms will be phased out—and companies will look for vendors offering PQC-supported security solutions. For example, the NIST already announced that RSA, EdDSA, and ECDH for digital signatures will be deprecated by 2030 and disallowed after 2035. There is growing concern that state actors could use CRQCs to hack federal databases and the like.
So the market has reached a point at which PQC will be required for certain markets, notably in critical infrastructures, while legacy architectures will remain a priority for most. As hardware security module manufacturers develop next-generation portfolios, are they supposed to create two distinct product categories—one for PQC and another for classic algorithms? ABI Research believes the more likely scenario is for vendors to increasingly offer crypto-agile solutions that can offer legacy, PQC, and hybrid alternatives.
Crypto-agile HSMs provide notable benefits:
- HSM vendors can easily update their solutions with new PQC standards as they emerge.
- HSM vendors can quickly replace broken PQC algorithms with others.
- Next-gen HSMs can continue to communicate with legacy systems through the support of hybrid schemes.
- Customers can extend the life span of products as legacy algorithms become banned, as the HSM can support PQC algorithms as well.
Takeaway: Legacy algorithms won’t be completely sunsetted for another decade, and will remain in use likely for another 20 to 30 years, though quantum threats will weigh increasingly heavily on the minds of organizations. By offering crypto-agile HSMs, vendors can acquire customers who continue using legacy algorithms, while carving a seamless pathway to PQC.
Final Word
Leading hardware security module vendors are rapidly upgrading their solutions with PQC-supported technologies. They are also applying these technologies to adjacent markets like Public Key Infrastructure (PKI). In the midst of this transition, vendors must take a step back and consider where the customer’s head is at.
When they see a vendor future-proofing HSMs, that’s surely a positive signal that the vendor is at the forefront of cybersecurity. But at the same time, most customers simply do not need quantum-safe HSMs as of yet. The early adopters stem from critical infrastructure markets, where data privacy is at its highest stakes.
Outside of these niches, customers will seek next-gen HSMs that can continue to support classical cryptographic algorithms. There is no incentive to pay a premium for cryptographic features you don’t need yet. But enterprise Information Technology (IT)/Operational Technology (OT) security teams surely know that quantum threats are on the horizon, making crypto-agile HSMs an attractive solution over the coming years.
For further analyst studies into quantum-safe HSMs and related security solutions, subscribe to ABI Research's Quantum Safe Technologies Research Service. Our analyst team provides clients with reports, competitive assessments, market data, content marketing, and advisory.
Related Research
The Quantum-safe Architectures of Hardware Security Modules
Frequently Asked Questions
Do hardware security module vendors have to support PQC?
Partially. Most HSMs vendors offer PQC libraries that end users can leverage, but not all are certified or standardized. Further, HSM vendors are not yet required to design quantum-safe architectures. Current certification programs like FIPS 140-3 and CC EAL do not mandate quantum-safe architectures, though they are pushing for support of PQC libraries. Most HSM vendors still need to prioritize classical algorithms since customer demand for PQC remains limited. Widescale support for PQC in HSMs is expected by 2030, but quantum-safe HSMs are likely not until 2035 to 2040.
What companies are supporting PQC algorithms and which are developing quantum-safe HSMs?
Leading companies include Crypto4A, Entrust, Futurex, IBM, IDEMIA, Kryptus, Marvell, Thales, Utimaco, and Securosys. Among them, Crypto4A stands out for building a fully integrated quantum-safe architecture, while others have introduced PQC algorithm support through firmware updates and early access programs to PQC libraries.
Why is crypto-agility important for HSMs?
Crypto-agility allows hardware security modules to support both classical and quantum-safe algorithms, ensuring a smooth transition as PQC adoption grows. It lets organizations maintain compatibility with legacy systems, while preparing for future quantum threats. Crypto-agile HSMs can easily add new PQC algorithms as they are standardized, replace broken algorithms, extend product life spans, and enable hybrid environments that balance current needs with future security requirements.


